HGAME 2019 week1

感谢杭电的师傅们举办的精彩比赛!
谁吃了我的 flag
根据题目提示想到应该是 vim 代码泄露,直接访问
1 | http://118.25.111.31:10086/.index.html.swp |
下载到题目的源代码,在 linux 下使用命令 vim -r index.html.swp 即可还原出 flag。
flag: hgame{3eek_diScl0Sure_fRom+wEbsit@}
换头大作战
考察了 header 的一些知识点,打开网页在输入框中随便写一点东西然后点击提交
提示需要使用 post 方式提交,使用 hackbar 提交,之后又会提示需要添加 XFF 头,构造下面的请求包:
1 | POST /week1/how/index.php?want=yes HTTP/1.1 |
接着又提示要使用 waterfox 浏览器访问,将 User-Agent 最后的 Firefox/64.0 改成 Waterfox/50.0 即可
接着要求从 哔哩哔哩来到这个网站,修改 Referer 为 www.bilibili.com 即可。
最后一步要求我们是 admin,将cookie 改成 admin=1。
flag: hgame{hTTp_HeaDeR_iS_Ez}
very easy web
题目给出如下代码
1 | <?php |
意思是要提交一个 get 类型的参数 id,并且不能包含字符串 vidar,但是在 urldecode 之后是 vidar。
非常简单,我们将 vidar url编码两次,原因是服务器接受到参数之后会自动解码一次,然后代码中再解码一次。
1 | http://120.78.184.111:8080/week1/very_ez/index.php?id=%2576%2569%2564%2561%2572 |
flag: hgame{urlDecode_Is_GoOd}
can u find me?
F12 找到另一个页面 f12.php,之后需要我们 post 一个密码,密码就在返回包的头部
1 | password: woyaoflag |
然后给出了一个链接,点进去说太快了,那么抓包再发送。
flag: hgame{f12_1s_aMazIng111}
brainfxxker
题目直接给了源代码,其实就是实现了一个 brainfuck 解释器,有关于 brainfuck 的语法在网上有很多。
分析给出的那段 brainfuck 代码就可以了,由于 “,” 是输入,所以把整个程序分成 9 段,每一段代表 flag 中的一个字符,通过上面的提示,使程序不输出任何内容的输入为正确的 flag,以第一段代码为例
1 | ,>++++++++++[<---------->-]<++[+.] |
每一段代码相当于实现了一个上面的方程,将 9 段代码全部分析出来之后即可得到 flag。
flag: hgame{bR4!NfUcK}
HelloRe
IDA 打开找到 flag。
flag: hgame{Welc0m3_t0_R3_World!}
わかります
这道题稍微有点费劲,关键代码如下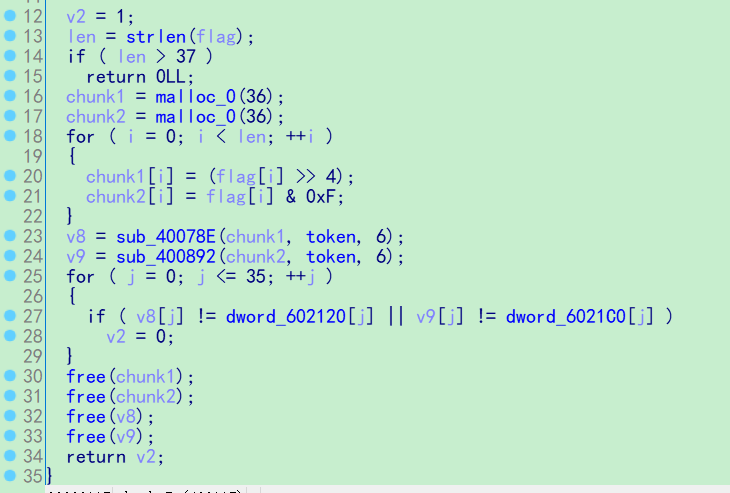
关键函数是中间的 sub_40078E 和 sub_400892。
本程序的基本逻辑是先将输入的 flag 进行两次不同的编码
1 | for ( i = 0; i < len; ++i ) |
分别保存在两个局部变量中,接着进入关键函数,第一个函数实现的是两个矩阵相乘,结果保存在 v8 中,第二个函数实现的是矩阵相加,由于两个矩阵都是 6 阶方阵,所以运算也相对简单,根据下面的方程
1 | enc_flag * token = dword_602120 |
现在 token 和最终的运算结果都已知,那么 flag 矩阵是可以求出的,求矩阵的方法有很多,我采取 Z3 进行约束求解
1 | from z3 import * |
flag: hgame{1_think_Matr1x_is_very_usef5l}
r & xor
简单的异或加密,需要注意一点,由于 IDA 的解析问题,有一部分 token 不能显示出来,需要动态调试得到。
1 | s = "hgame{Y0u_mayb3_need_th1s_0ne!!!!!}" |
flag: hgame{X0r_1s_interest1ng_isn’t_it?}
Pro的Python教室(一)
把代码中的 enc2 BASE64 解密即可。
flag: hgame{Here_1s_3asy_Pyth0n}
babysc
主函数代码不能正常 F5,提示有一处 call 分析失败,将它 nop 掉之后再 F5 ,得到如下伪代码
1 | int __cdecl main(int argc, const char **argv, const char **envp) |
大概的意思就是把输入进行异或加密,最后的 call 应该是跳转到用户的输入继续执行。
先把输入的 shellcode 异或就行。
1 | # coding=utf-8 |
flag: hgame{Baby_Baby_S0_E4ay!}
aaaaaaaaaa
连上去输入 100 个 a 就可以了。
1 | # coding=utf-8 |
flag: hgame{Aa4_4aA_4a4aAAA}
薯片拯救世界1
除了那些花里胡哨的东西之外,逻辑就是先把 flag 读取到一个全局变量里面,然后进入一个循环,要求我们输入 flag,并且使用 strncmp 函数和 flag 比较。
由于比较的字节数是由 strlen 确定的,可以通过控制输入长度来爆破 flag。
1 | # coding=utf-8 |
flag: hgame{Ch1p_1s_Awakking!}
Steins;Gate
这道题考察的东西比较多,类似闯关一样分成四关,第一关代码如下
1 | unsigned __int64 sub_4008F6() |
要求 v2 == 9011,通过上面的 read 栈溢出控制 v2,但是不能直接控制返回地址,因为程序开启了 canary。
第二关代码:
1 | unsigned __int64 sub_400958() |
通过格式化字符串漏洞泄露出 rand 出的数值,然后栈溢出控制 v4 满足要求。
第三关:
1 | unsigned __int64 sub_400A00() |
这里通过动态调试发现,v1 的值正好在上一关中 buf 的范围内,所以在上一关就构造好 payload 满足这里的条件,之后利用 5 字节的格式化字符串漏洞泄露 canary。
最后一关和第一关一样,不同的是已经拿到了 canary,构造满足条件的 payload 然后栈溢出即可。
程序中有 system 函数
1 | int __fastcall sub_400A76(const char *a1) |
只需要找一个 pop rdi, ret 的 gadget
1 | # coding=utf-8 |
flag: hgame{El_PsY_C0NgrOO}
Hidden Image in LSB
简单的 LSB 隐写,用 stegsolve 打开就可以看到 flag。
flag: hgame{LSB_is_easy_for_u}
打字机
给出了两张图片
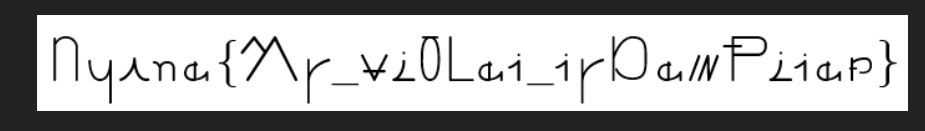
第一张看上去像某种打字机,然后打出了 flag,谷歌识图之后发现这个打字机是某部动画片里的?
在知乎上找到一篇文章
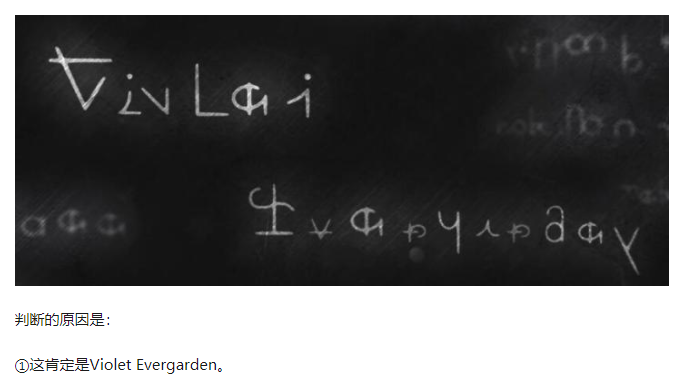
通过这两张图片慢慢看(猜)就能看(猜)出 flag。(打字机上印的是大写,而 flag 中有小写字母…)
flag: hgame{My_vi0let_tyPewRiter}
Broken Chest
压缩包题目,不能正常解压,用 010 editor 打开看到压缩包头部的 PK 变成了 OK,改回来之后再解压(密码在 winrar 右面的注释栏里面 S0mETh1ng_U5efuL),即可得到 flag。
flag: hgame{Cra2y_D1aM0nd}
Try
首先分析流量包,从里面提取出一个压缩包 dec.zip,解压后是另外一个带有密码的压缩包和 password.txt,提示密码是 hgame 后面跟着 8 个不知道是什么的字符。
猜测是 8 位数字,用 ZIP 密码破解工具的掩码模式破解出密码 hgame25839421
出来一张图片,binwalk 还可以从图片提取出来另一个压缩包,直接解压需要密码,使用 winrar 修复压缩包之后就可以正常解压了,最后得到一个 word 文档,将后缀名改成 zip 解压出来一堆文件,在 word 文件夹下的 document.xml 中找到 flag。
flag: hgame{59d28413e36019861498e823f3f41406}
Mix
摩斯密码 –> 十六进制转字符串 –> 栅栏密码解密 –> 凯撒密码解密
flag: hgame{E4sY_cRypt0}
perfect_secrecy!
提示 OTP 密码,即一次性密码本,银行的一些动态口令使用的就是 OTP 加密。
给出的脚本如下
1 | import binascii |
大概意思就是声明了一个随机数作为 OTP 的密钥,用同一个密钥将一首诗和 flag 进行加密。
google 一圈发现了几道类似的题目,基本思想是 OTP 虽然安全,但是如果一个密钥被用来加密许多明文的话,就面临很大的风险了,有一种攻击叫做 cribdrag,就是专门用来攻击 OTP 类似的密码的。
在 github 上面可以找到 cribdrag,但是用在这道题目上并不好使,我找到了另外一个脚本
1 | #!/usr/bin/python |
脚本解出来的 flag 是
1 | *TP_:s_not_safe_if_more_tha&_once |
把几个字符修复一下
flag: hgame{OTP_is_not_safe_if_more_than_once}
Base全家
给出一个很大的文件,里面是很多层编码嵌套起来的,推荐到这里解密。
flag: hgame{40ca78cde14458da697066eb4cc7daf6}
- Title: HGAME 2019 week1
- Author: Catalpa
- Created at : 2019-02-02 00:00:00
- Updated at : 2024-10-17 08:49:46
- Link: https://wzt.ac.cn/2019/02/02/hgame-2019/
- License: This work is licensed under CC BY-SA 4.0.